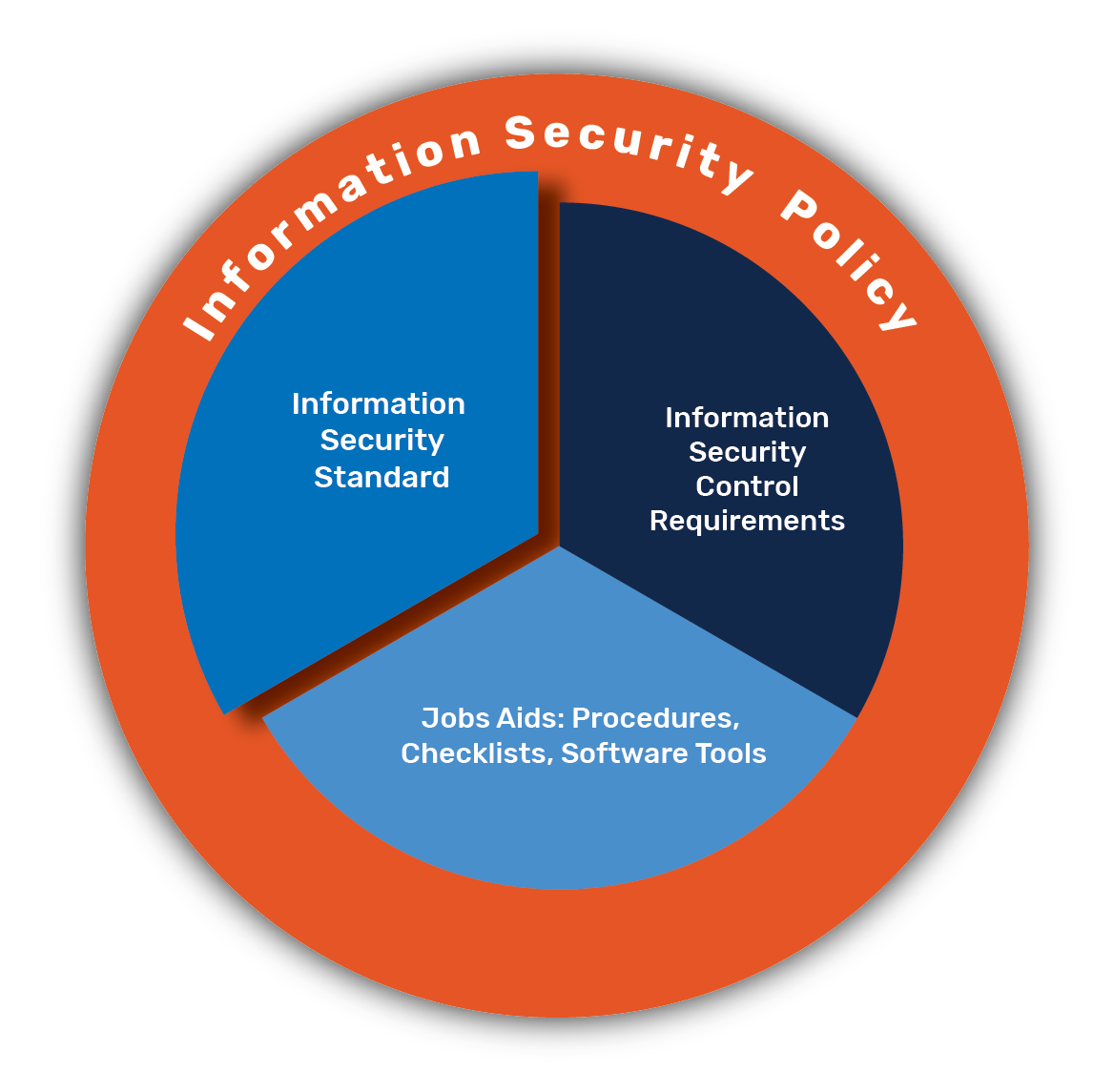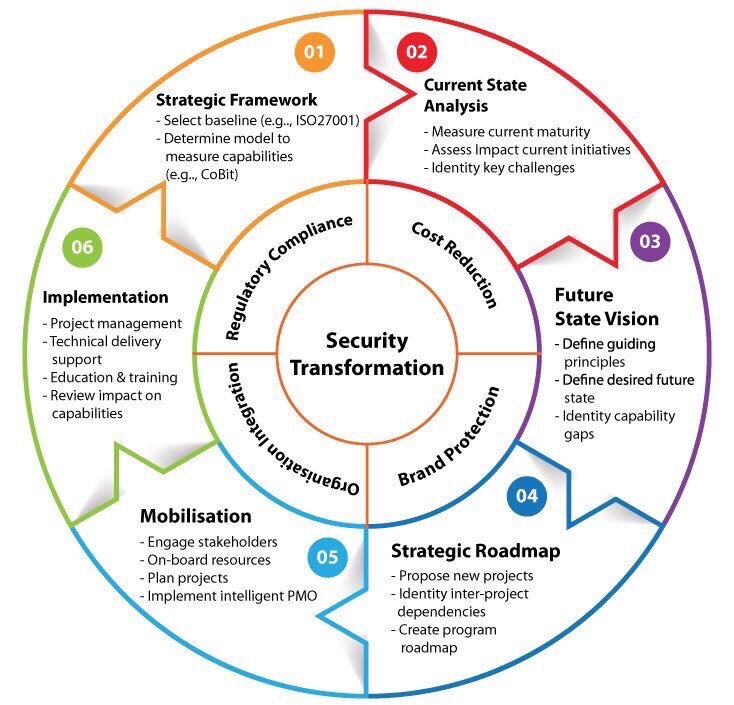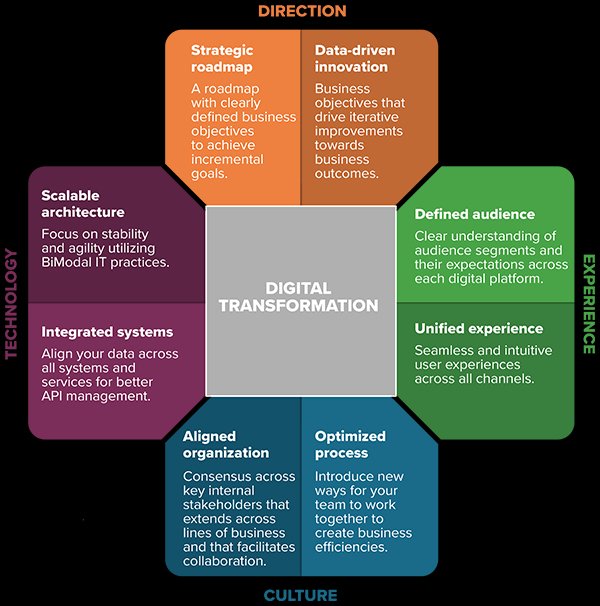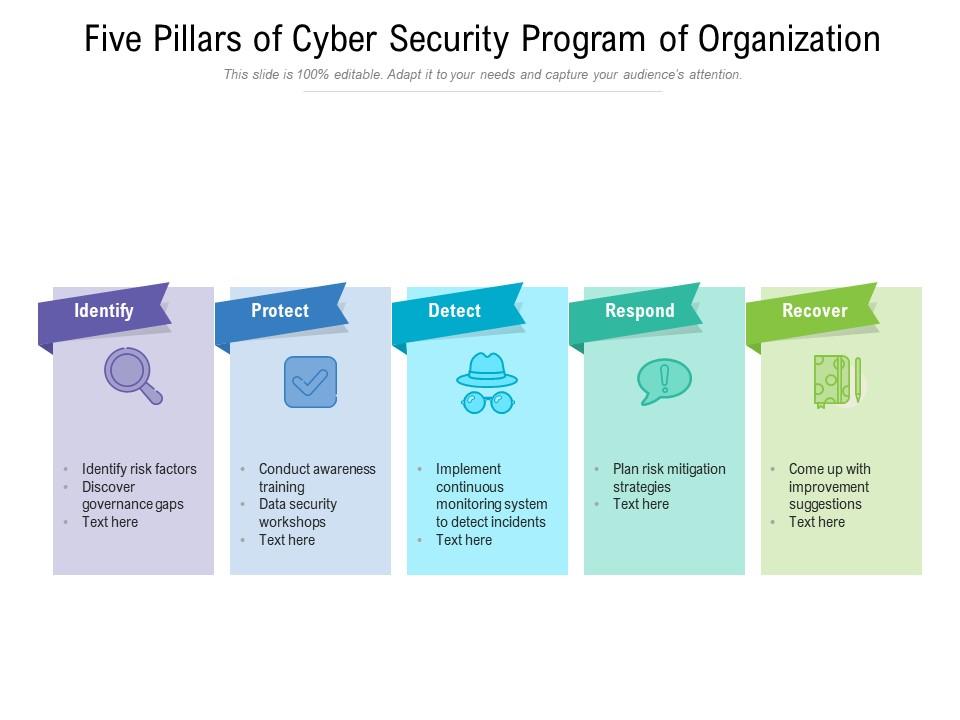
Five Pillars Of Cyber Security Program Of Organization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

NYU Tandon Online on Twitter: "7 days left to the 11th #NYUCyberLecture! Find ways to use data science fundamentals in cyber security programs with us on October 6, 2021, at 1-2:30 pm



![Withdrawn] 10 Steps: Summary - GOV.UK Withdrawn] 10 Steps: Summary - GOV.UK](https://assets.publishing.service.gov.uk/government/uploads/system/uploads/image_data/file/35242/10_steps_to_cyber.png)
![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2020/08/visual-representation-of-data-privacy-and-data-security-areas.png)